Sep 22, 2022
System Utilities: Overview and the Tailscale Backbone
This series of blog posts is going to describe a little bit about my home networking solution and different applications and tools that I run to make my life a little bit easier.
I like self hosting things on my network for a range of reasons. Partially it’s because I like to pretend I’m a sys-admin without any actual consequences for when things go wrong and everything fails dramatically (much better than having to deal with a critsit and lots of angry customers at least); and part of me just likes the level of control and being able to tinker with things.
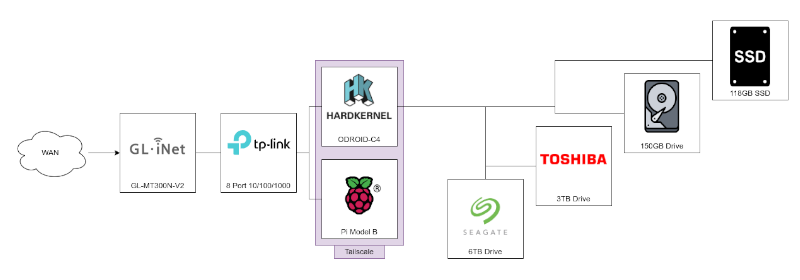
My home network is pretty limited but it does the job it needs. The network itself is run from a GL.iNet GL-MT300N-V2 (Mango) which provides wired and wireless connectivity throughout the network. I chose this one because it was cheap, only needed to serve a single room and also had built in support for WireGuard VPN configurations which meant I could apply NordVPN configurations at the network boundary which is incredibly helpful.
For wired connectivity, this then runs into a simple unmanaged TP-Link 8-Port 10/100/1000Mbps Switch which connects up to my main PC, and the two primary pieces of my infrastructure.
The bulk of my services run off an ODROID-C4 which was my first upgrade from my old Raspberry Pi Model B. The ODROID-C4 is then connected to 4 external drives, a 6TB Seagate, a 3TB Toshiba, a 118GB SSD, and a 150GB disk giving a combined external storage of 9.2TB, on top of 60GB storage on an SD card for the OS.
The next infrastructure device is the previously mentioned Raspberry Pi Model B. This is now pretty dated and unfortunately couldn’t run as much as I wanted to throw at it. For the time being, this only runs a single DNS resolver which resolves local network domains which allows me to use wildcard domain names which has been an incredibly helpful development on my network. The internal DNS runs simply off a stock install of dnsmasq with the simplest configuration I could set up.
1 | address=/droid.olympus.lan/100.xxx.xxx.xxx |
The most important bit of this configuration (as hinted in the title) is actually a service I stumbled upon by accident on Twitter after seeing a few tweets from one of its creators: Tailscale. They describe themselves as “a VPN service that makes the devices and applications you own accessible anywhere in the world, securely and effortlessly” and they are right. Each of my devices is signed into my Tailnet which gives them all a seamless local network, accessible over 100.x.x.x IPs, guaranteed to be internal only to me.
This is where the custom DNS resolver comes in as well, for the time being Tailscale doesn’t have built in DNS functionality suitable to my needs. Every device is given a domain name by them, however I wanted custom domains with the ability to have wildcard subdomains. However they do support Split-DNS which means I can declare a DNS server to use for domains matching a suffix, so in this case I defined my local network as ‘.olympus.lan’ and any domain matching that gets shipped, vai Tailscale, to my Pi which will return the Tailscale IP of the matching device. And as the IPs are fixed to devices and nearly guaranteed not to change - this has been set up and left without issue (I haven’t even touched the Pi outside of updates in months!).
This small network configuration is currently running 10 web services, 2 databases and more all with ease. There will be a series of posts following this one focussing on different services and setups in my home network, part as documentation and partly seeing these services in production.







